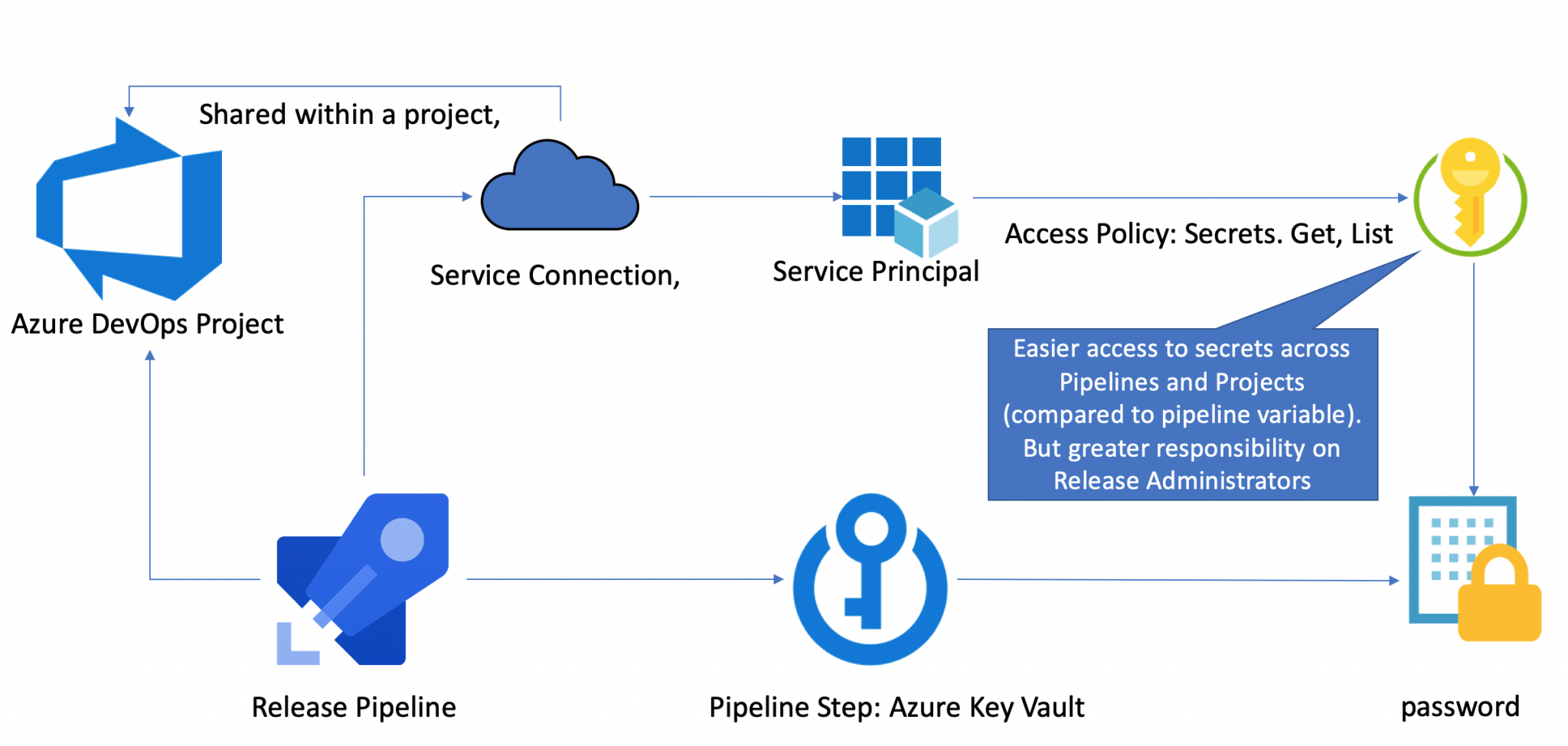
Rbac abac difference comparitech What is azure key vault? Use azure key vault secrets in pipeline activities key vault access policy vs rbac
Grant permission to applications to access an Azure key vault using
Permanently delete a key vault in azure using powershell – 4sysops Using azure rbac with azure key vault Rbac vs abac: what's the difference? (a guide to access controls)
Azure key vault access policy vs rbac
Grant permission to applications to access an azure key vault usingWhat is role based access control rbac vs abac Building an issuer websiteGrant permission to applications to access an azure key vault using.
Azure rbac vs azure policies vs azure blueprints (2022)將應用程式存取權授與 service fabric 受控叢集上的其他 azure 資源 Azure automation preparing modules for first use at millicentrhilton blogAzure key vault access policy vs rbac.

Vault azure certificates hsm certificats powershell manage secrets complex
Assign an azure key vault access policy (cli)Using a certificate to connect dataverse azure key vault access policy Using a certificate to connect dataverse azure key vault access policyVault assigned subscription arm nested provision.
Azure vault rbac keyvaultAssign an azure key vault access policy (cli) App service key vault certificate supports rbac model · issue #91175Grant permission to applications to access an azure key vault using.

Abac vs rbac: the advantage of attribute-based access control over role
Use nested arm template to provision user assigned managed identity andPolicy based management model role based access control rbac models Blog postsEnable a customer-managed key.
Back up azure key vault secretsWhat is role based access control rbac vs abac Authenticate to azure key vaultProvide access to your key vault with azure role-based access control.

Grant permission to applications to access an azure key vault using
Rbac vs abac: pros, cons, and example policiesNodejs中nosql数据库的基于角色的访问控制(rbac) role-based access control ( rbac) for Vault key azure policy access create secrets enlarge click backupAzure key vault rbac (role based access control) versus access policies.
Comparing azure rbac, azure policy & azure blueprintsVault azure Policy based management model role based access control rbac models.